Overview
The Private Specialized Small Language Model (SLM) architecture is a secure and local framework designed to manage and process sensitive customer data without external outputs. This documentation provides a detailed analysis of the architecture’s components, security features, integration with local systems, and compliance with various regulatory requirements. The SLM is specifically built to operate within a controlled environment, ensuring data privacy and robust control over information processing.
1. Introduction to the Private Specialized SLM Architecture
The Private Specialized SLM architecture is designed to meet the needs of organizations managing sensitive data that require elevated levels of security and privacy. Unlike traditional language models that often depend on cloud-based infrastructure, the SLM operates entirely within a local environment. This approach is particularly beneficial for organizations bound by strict regulatory requirements, such as GDPR, CCPA, and HIPAA, which mandate stringent data privacy and security measures.
By processing all data locally, the SLM eliminates the risks associated with external data transmission, including potential data breaches and unauthorized access. This architecture not only enhances security but also ensures compliance with various data protection laws. Additionally, the SLM architecture is tailored to integrate seamlessly with local applications and databases, providing a robust solution for secure and efficient data processing.
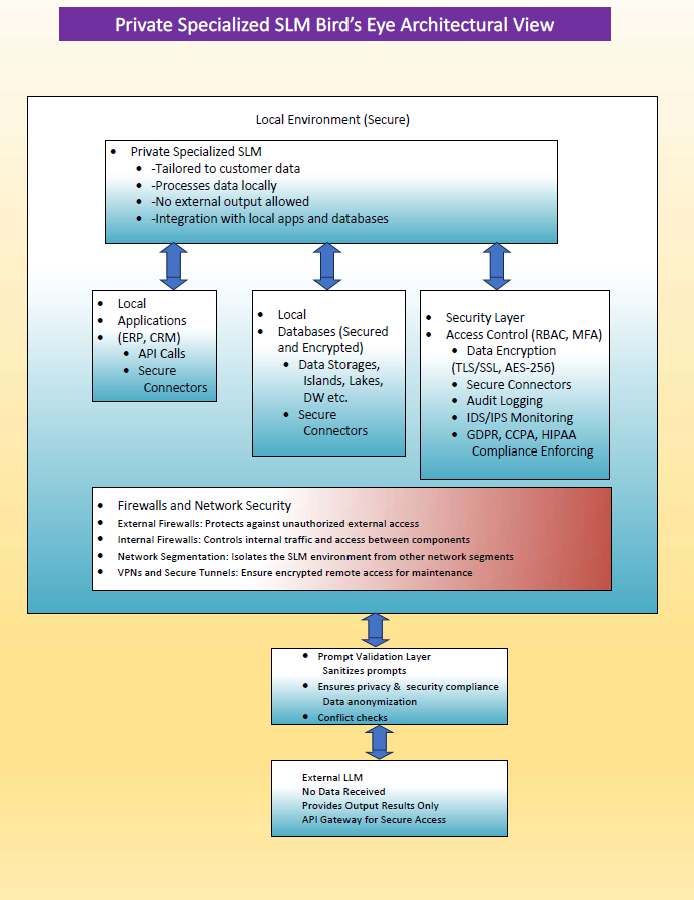
2. Architectural Design and Core Components
The architecture of the Private Specialized SLM is built around several core components, each serving a specific function to ensure secure and efficient data processing. The key components include local environment integration, secure data handling mechanisms, a comprehensive security layer, and a prompt validation layer. These components work together to provide a secure framework for processing sensitive customer data.
Local environment integration allows the SLM to interact directly with local applications such as ERP (Enterprise Resource Planning) and CRM (Customer Relationship Management) systems. Secure connectors and APIs facilitate communication between these systems and the SLM, ensuring that data remains within the local environment. The security layer includes access control, encryption, and monitoring features to protect data from unauthorized access and potential threats.
3. Integration with Local Applications
The integration of the SLM with local applications is a critical aspect of its architecture. This integration is achieved through secure API calls, which enable the SLM to interact with existing applications such as ERP and CRM systems without exposing sensitive data to external threats. By processing data locally, the SLM ensures that sensitive information remains within the organization’s infrastructure, reducing the risk of data breaches.
Moreover, the integration with local applications allows for real-time data processing and analysis, enhancing the efficiency of business operations. This seamless integration is particularly beneficial for organizations that rely on real-time data insights to make informed business decisions. By leveraging existing local applications, the SLM provides a cost-effective solution for secure data processing without requiring significant changes to the existing IT infrastructure.
4. Secure Data Handling and Processing
Data handling in the Private Specialized SLM architecture is conducted entirely within a secure, local environment. The architecture ensures that all data processing activities are performed on-site using local resources, eliminating the need for external data transfers. This approach minimizes the risk of data breaches and ensures compliance with various data privacy regulations.
The SLM is equipped with advanced mechanisms for secure data processing, including data anonymization and conflict checks. Data anonymization techniques are employed to protect user privacy, while conflict checks help prevent incorrect or malicious data processing. These mechanisms ensure that sensitive data is managed securely and efficiently, providing a robust solution for organizations that require high levels of data security.
5. Secure Connectors and API Management
Secure connectors and API management are essential components of the SLM architecture, providing a secure means of communication between the SLM and other local systems. Secure connectors ensure that all data transfers are encrypted and that only authorized systems can communicate with the SLM. This approach reduces the risk of data interception and unauthorized access.
The architecture also incorporates API management features to control and monitor API usage. These features include rate limiting, API key management, and logging of API activity. By managing API usage, the SLM ensures that only authorized users and systems can access its data and functionality, enhancing security and compliance with regulatory requirements.
6. Security Layer: Access Control and Encryption
The security layer is a critical component of the Private Specialized SLM architecture, providing multiple layers of protection to secure sensitive data. This layer includes robust access control measures such as Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA), ensuring that only authorized personnel can access the SLM and its data.
In addition to access control, the security layer employs advanced encryption techniques to protect data both in transit and at rest. Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols are used to encrypt data in transit, while Advanced Encryption Standard (AES-256) is used for data at rest. These encryption measures ensure that sensitive data remains secure and protected from unauthorized access and potential breaches.
7. Network Security and Firewall Configuration
Network security is a fundamental aspect of the SLM architecture, designed to protect the SLM environment from external and internal threats. The architecture employs multiple layers of network security, including external and internal firewalls, to control the flow of data and prevent unauthorized access.
External firewalls protect the SLM environment from unauthorized external access, ensuring that only legitimate traffic reaches the SLM. Internal firewalls, on the other hand, control the flow of data between internal components, preventing unauthorized access and potential lateral movement by attackers within the network. This dual-layer firewall approach provides a robust defense against both external and internal threats.
8. Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are integral components of the SLM architecture, providing real-time monitoring and protection against potential threats. These systems are designed to detect and respond to suspicious activity, preventing unauthorized access and protecting sensitive data from cyber-attacks.
The IDS/IPS systems monitor network traffic and system activities for signs of malicious behavior, such as unauthorized access attempts, data breaches, and other security incidents. When a potential threat is detected, the IPS component takes immediate action to block or mitigate the threat, ensuring the security and integrity of the SLM environment.
9. Prompt Validation and Data Sanitization
The Prompt Validation Layer is a unique feature of the Private Specialized SLM architecture, designed to sanitize input prompts and ensure compliance with security and privacy standards. This layer plays a crucial role in preventing malicious input from compromising the security of the SLM.
Data sanitization techniques are employed to ensure that input data does not contain any malicious content or sensitive information that could lead to security breaches. The Prompt Validation Layer also includes mechanisms for data anonymization, which helps protect user privacy by removing personally identifiable information (PII) from input data. By validating and sanitizing input prompts, the SLM ensures that only secure and compliant data is processed.
10. Compliance with Regulatory Standards
Compliance with data protection regulations is a key aspect of the Private Specialized SLM architecture. The architecture is designed to meet the requirements of various data privacy laws, including GDPR, CCPA, and HIPAA. This compliance is enforced through a combination of technical and organizational measures, such as access controls, encryption, and audit logging.
The SLM architecture also supports regular compliance audits to ensure that all components continue to meet regulatory requirements. These audits involve reviewing system configurations, access logs, and other relevant documentation to verify compliance with data protection laws. By maintaining compliance with regulatory standards, the SLM helps organizations avoid legal penalties and maintain customer trust.
11. Integration with External Systems and LLMs
While the Private Specialized SLM is primarily designed for local data processing, it can also integrate with external systems under strict controls. An API Gateway provides secure access to external systems, ensuring that any interactions are tightly controlled and monitored. This gateway acts as a protective barrier, allowing the SLM to receive external outputs without exposing any internal data.
The architecture also supports integration with external Large Language Models (LLMs) when necessary. However, this interaction is carefully managed to ensure that no data is sent back to the external LLMs, preserving the privacy and security of the local environment. By leveraging the capabilities of external LLMs while maintaining strict security controls, the SLM provides a flexible and secure solution for data processing.
12. Logging, Monitoring, and Audit Trails
Logging and monitoring are essential components of the SLM architecture, providing visibility into system activities and helping to detect potential security incidents. The architecture includes comprehensive logging capabilities to record all access and changes to the system, providing a detailed audit trail for compliance and security purposes.
Monitoring tools are also integrated into the SLM environment to provide real-time visibility into system performance and security. These tools help detect anomalies and potential security threats, allowing for quick response and mitigation. By maintaining detailed logs and monitoring system activities, the SLM ensures the security and integrity of the data processing environment.
13. Firewalls and Network Segmentation
Firewalls and network segmentation are crucial components of the SLM architecture, providing multiple layers of protection to secure the SLM environment. External firewalls protect the SLM environment from unauthorized access, while internal firewalls control the flow of data between internal components.
Network segmentation is also employed to isolate the SLM environment from other network segments, reducing the risk of cross-contamination in case of a security breach. This segmentation helps contain potential threats and prevents them from spreading to other parts of the network. By implementing firewalls and network segmentation, the SLM architecture provides a robust defense against both external and internal threats.
14. VPNs and Secure Tunnels for Remote Access
To facilitate remote management and updates, the architecture supports Virtual Private Networks (VPNs) and secure tunnels. These technologies provide encrypted channels for remote access, ensuring that maintenance activities do not compromise the security of the SLM environment.
VPNs and secure tunnels are particularly useful for organizations with distributed teams or those requiring remote access capabilities. By providing a secure means of remote access, the SLM architecture ensures that all maintenance activities are conducted securely, without exposing the system to external threats. This approach provides a flexible and secure solution for managing the SLM environment.
Conclusion
The Private Specialized Small Language Model (SLM) architecture offers a comprehensive, secure solution for organizations that require strict data privacy and security controls. By processing data locally and integrating seamlessly with existing local applications and databases, the SLM ensures that sensitive information remains protected. The architecture’s robust security measures, including secure connectors, a security layer, prompt validation, and compliance enforcement, provide a multi-faceted approach to data protection. This documentation provides a detailed overview of the architecture’s components and features, illustrating its suitability for environments where data security and privacy are paramount. This architecture designed and implemented by AlpineGate AI Technologies Inc. for AlbertAGPT LLM model’s use for sectoral based solutions.